Rethinking Security
Personal Cybersecurity - Make Yourself Invisible to Hackers
Web / SaaS Platforms - Invisible Passwordless MFA for Growth
One invisibility architecture for individuals and the platforms they use.
VanishingPoint Security – Invisible by Design
A new class of Fortified VPNs that makes you invisible to hackers and surveillance, even on compromised devices and networks—whether banking, traveling, or handling sensitive data.
✔ Shield yourself on unsecured networks—Wi-Fi or Global Roaming
✔ Open suspicious links and emails without risk
✔ Keep your data private—whether working or traveling
✔ No software to install—access instantly from any device
Make yourself invisible to hackers and surveillance
— even on compromised devices and unsecured networks.
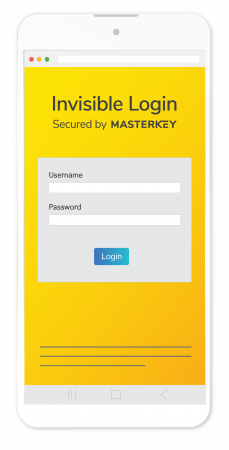
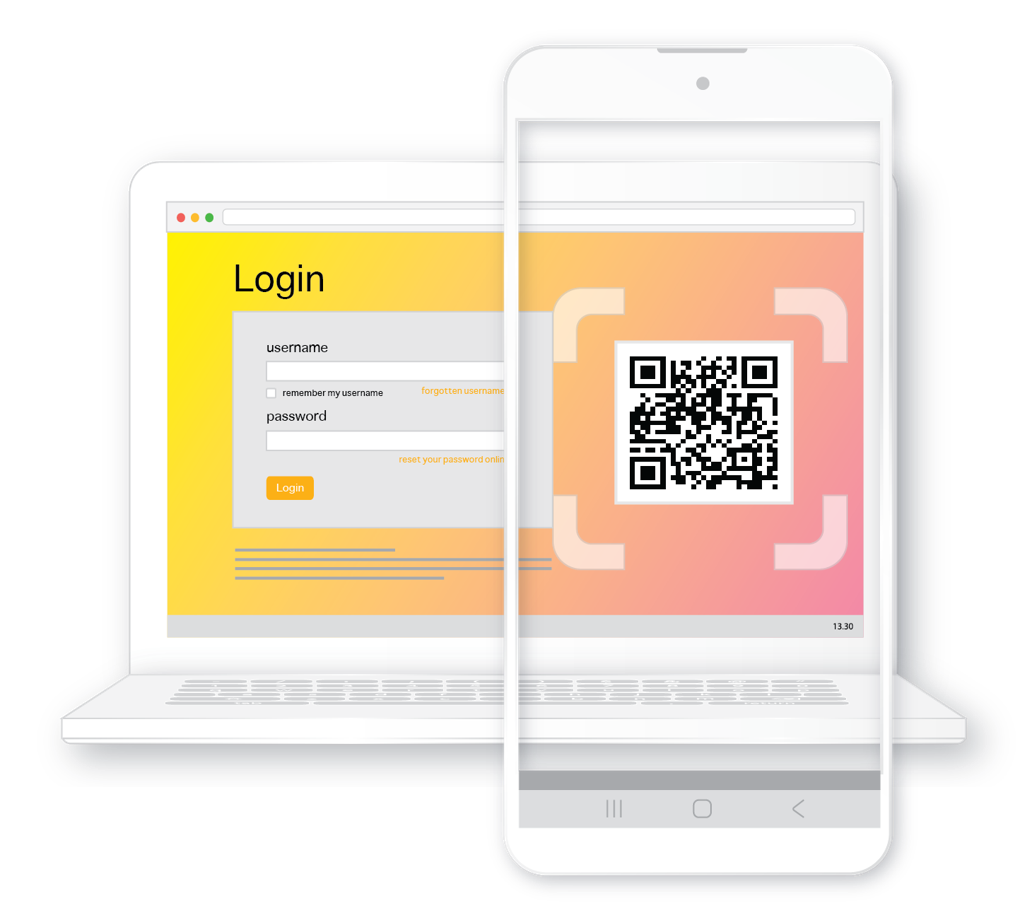
MasterKey – The future of secure, seamless authentication.
A next-generation passwordless login that turbocharges growth by doubling customer acquisition—eliminating friction and increasing engagement.
✔ 2FA in one step (not two steps)—no software, no setup
✔ Invisible to users—completely frictionless
✔ Deploys in minutes (not months)
✔ Instant visitor onboarding—eliminates registration abandonment
Invisible Passwordless Authentication (with MFA)
— doubling customer acquistion with instant onboarding.
Who is BankVault?
BankVault is a deep-tech cybersecurity company pioneering intelligent new approaches to web security.
We hold 15 granted patents worldwide and are backed by Turing Laureate Whitfield Diffie, co-inventor of public-key cryptography, as shareholder and advisor. That momentum was reinforced by selection as one of the world’s Top 60 Deep-Tech Startups, Top 1% of 6,800 companies, by Enterprise Singapore at SLINGSHOT 2025. A newly granted U.S. patent protecting MasterKey’s core innovation further strengthens that position.
BankVault’s invisibility architecture is built on more than 35 proprietary innovations, with additional breakthroughs in development. It eliminates attack surfaces to secure individuals from hackers and surveillance, and to deliver Invisible Passwordless MFA for web applications that provides frictionless access and accelerates SaaS growth.
BankVault operates from San Francisco, Silicon Valley and Perth, Western Australia.
TOP 60 Global Deep-Tech Startup - SLINGSHOT 2025 (Top 1% of 6,800 companies by Enterprise Singapore)


Best Overall Innovation - Indo-Pacific Maritime Defence Expo hosted at the Sydney ICC 2022


Top Fintech Startup Worldwide - World Cup Tech Challenge hosted by Silicon Valley Forum and Microsoft 2016


Winner – CyberTech Demo Day NYC
VentureOut NYC CyberTech 2020



“BankVault’s story is one of perseverance with a solid underlying technology”

Test Drive
Get hands-on experience with guidance from a cybersecurity consultant