Live Demo – BankVault Invisible Keyboard for Webservers
Live Demo
Webserver Encrypted Keyboard
(Passwordless Demo – please contact an Advisor)
Type anything into the username / password fields and press enter.
The demo shows what was captured by the webserver, including the unique signature of the device. Context only exists inside the webserver to merge the username, password and device signature together to log the user in.
Multi-Factor Authentication (MFA/2FA) is invisible to the user.
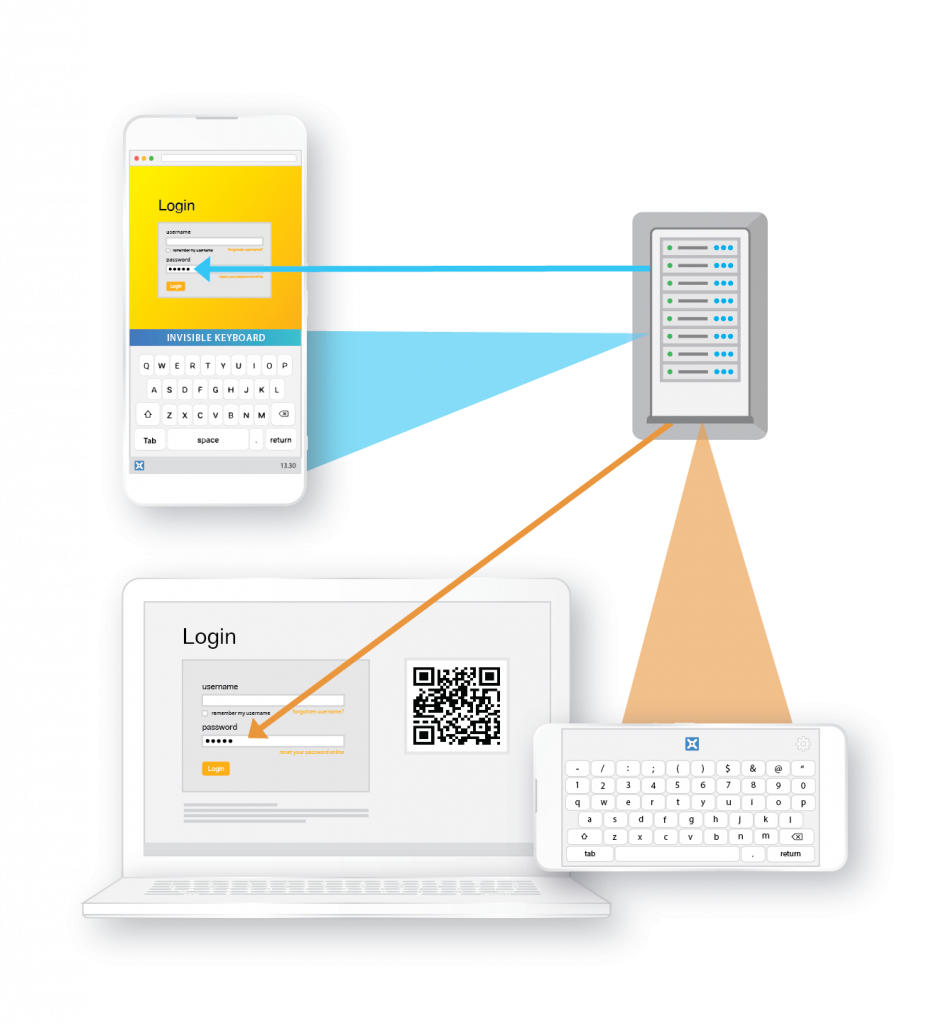
Webservers automatically offer mobile or workstation login pages.
This demo deliberately overrides this automation.
Are you on a Mobile?

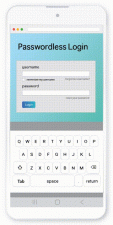
Enter anything for the username and password.
The password keyboard is an illusion projected by the webserver into the mobiles local browser.
The demo echoes the data captured by the webserver: username, password, mobile device signature.
The webserver can morph the keyboard image to add additional layers of security. E.g. morphing the image.
Are you on a Workstation?
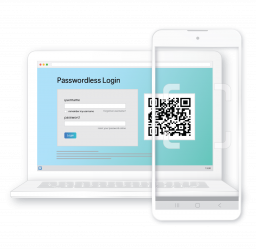
If you are accessing this page from a workstation, click the green button.
Enter anything for the username and password.
The user name allows keyboard entry, the password does not.
The demo echoes the data captured by the webserver: username password, mobile device signature
The webserver can morph the keyboard image to add additional layers of security. E.g. morphing the image.
* If your camera can’t read a QR scanner then download the BankVault Keyboard app or another QR scanner.


