Hacking 2FA and Account Takeovers
|
How it Happens
The weakest link in online services is the end-user device. Each PC and smartphone is unique in its versions of firmware, drivers, operating system, applications, and live Internet connections. Consequently no-one can guarantee a device hasn’t been compromised because todays most sophisticated threats are actually from legitimate code (called non-malware) which is undetectable. It has permission to do almost anything. Websites are blind as to whether a user’s device has been compromised and shared, and whether a login is actually coming from a customer or an impersonator.
When we enter user credentials into an online form the asterisks that appear are just a mask for human eyes to hide the password content from someone looking over our shoulder or capturing an image of our screen. Surprisingly, it is just clear-text in the browser and isn’t even transmitted to the website until after the login button is pressed. Any software in the browser intercepts this instantly.
Today every website and most apps use JavaScript to create interactive experiences. If JavaScript code is injected by a hacker into a website the users device executes it instantly. This non-malware is legitimate code, and there’s no defence because a machine can’t tell what it will do until it executes. According to Symantec JavaScript injections, also called Drive-by-Download or Man-in-the-Browser attack, on average run 10-months before the hacker stings their victim. During this time they easily capture login credentials and can then trick user’s into revealing their second security step (2FA).
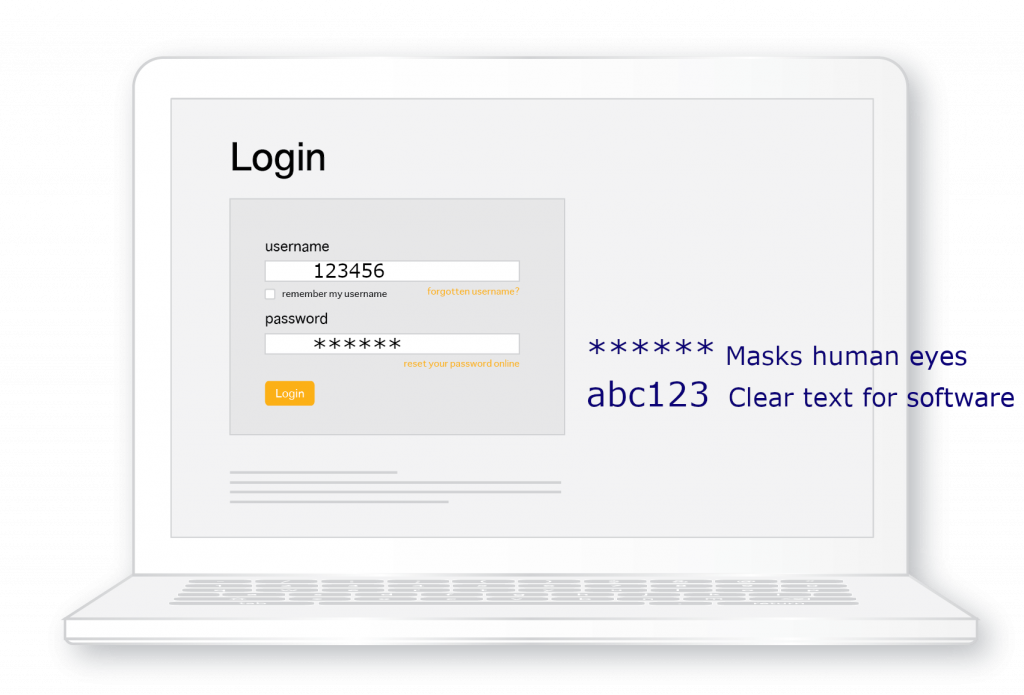
Password Managers cannot secure this. These encrypt and store our passwords but the moment they load a web-form the password has to be inserted as clear-text. This is immediately exposed to any software in the browser.
This fundamental design flaw in web-browser security cannot be patched.
Password Manager






2FA isn’t Enough
The industry’s solution to preventing account takeovers is 2FA or Multi-Factor Authentication — something you have (smartphone or FOB), something you know (password) and perhaps something you are (biometrics). Most attacks involve tricking the user into revealing their one-time-passcode and biometrics, which are then harvested and reused:
Example – Hacker redirecting payments
When a user uploads list of creditor bank accounts to pay a Man-in-the-Browser changes the account numbers behind the screen. When the user authorizes payment with their banking FOB or SMS text, the money goes to the wrong accounts. The user then has to prove that they’re not defrauding the bank as they did, after all, authorized the payment.
Example – Hacker capturing One-Time-Passcode
It’s simple to capture login credentials to online accounts using a key logger, clipboard reader, or JavaScript in the browser. According to Symantec, non-malware hackers on average collect data for 10 months before stinging their victim and during this period are undetectable. The day they strike will be the day there’s a spike in the users bank balance. When the user logs in the hacker in the browser asks for the one-time-passcode. The user thinks it’s their institution and hands over the one-time-passcode from their FOB, Yubikey, Google Authenticate, etc. One-time-passcodes are issued once but can be used multiple times in the next 35 seconds.
Biometrics – No Magic Bullet
Even a unique biometric identifier such as a fingerprint, voice, hand scan or face scan is just a data file. It typically forms one element of a MFA solution and, being a data file, it can be intercepted and re-used by injecting into a system.
Many security professionals are concerned about the user of biometrics in public facing systems. Even a hashed version of your fingerprint stored on a server creates an attack point outside your control and there is always going to be another security breach where sensitive personal data is lost to the hackers. A couple of recent high-profile attacks were:
- Equifax USA which suffered the largest cyber breach in history exposing the financial records of 163 million US citizens. Their roadmap was to be the authority for identity, including everyone’s biometric records.
- Suprema Korea which controls the entry and exit to 1.5 million secure areas within buildings worldwide lost 27 million personal identity data records, including 1 million unencrypted fingerprints.
The day you lose your iris scan to the hackers you've lost your identity forever.
How to Stop Account Takeovers and 2FA Hacking
Cybersecurity dynamics fundamentally change when user credentials can never be intercepted by malware on any device.
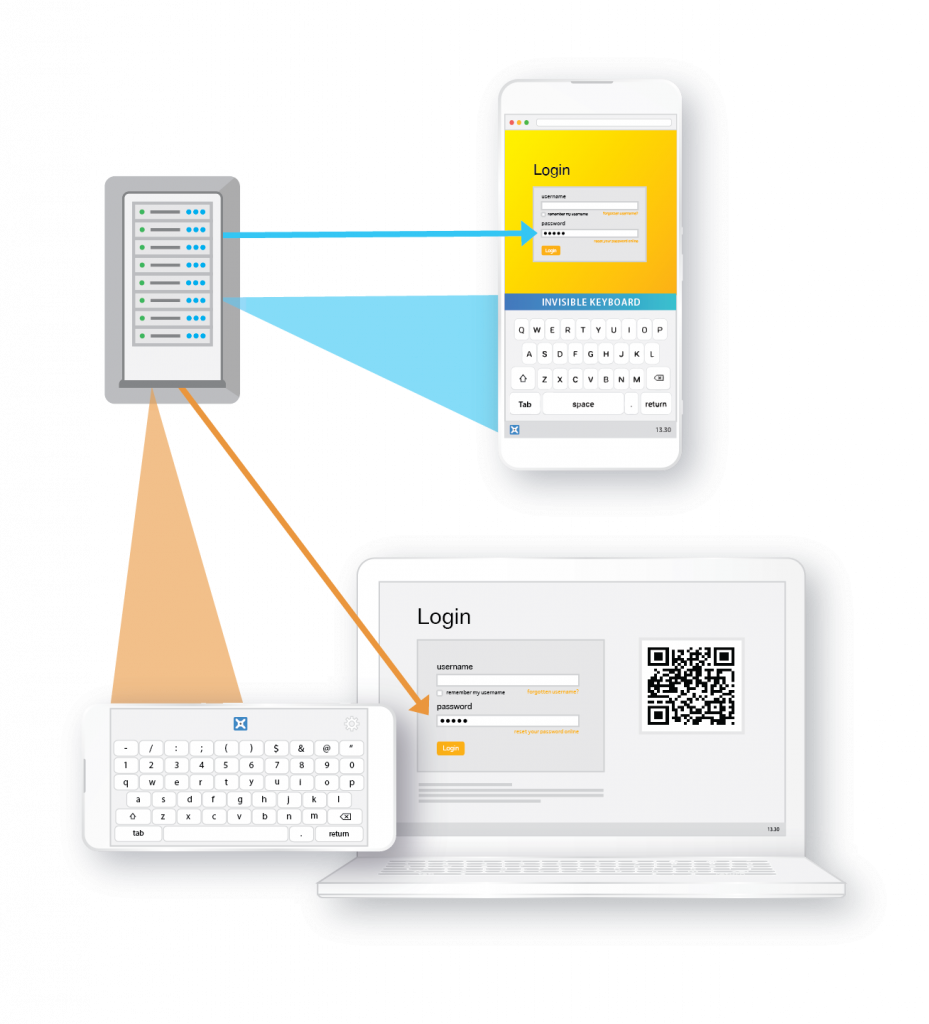
INVISIBLE KEYBOARD FOR WEBSERVERS is a seamless, radically simple approach to IAM (Identity & Access Management) security enabling Passwordless logins and securing vital user input like Passwords, PINs, SSN’s, CCVs, – without deploying any client software or infrastructure changes.
The system inverts webserver-browser architecture, harnessing a user’s mobile as an input device. An illusion of a keyboard is created on the phone but user actions only generate characters inside the webserver which echoes asterisks onscreen. There’s nothing on the user’s devices to intercept. Context only exists inside the webserver to merge username, password and device signature together to log the user in. Multi-Factor Authentication is invisible to the user.
- No client software
- No infrastructure changes.
- Simple, fast deployment.
The webserver integration is 20 lines of code which can be done in as many minutes. It prevents the 6 major attack vectors targeting Identity Theft and Account Takeovers:
- Keyloggers
- Man-in-the-Browser
- Bots
- Screen scraping
- Man-in-the-Middle
- Phishing
You can’t hack something that doesn’t exist.
How to Empower Users to Take Control of Their Own Security
How can you tell if your computer is compromised? You can’t!
When we open emails or click web hotlinks we risk exposure to threats which anti-virus software can’t detect. The proliferation of ransomware demonstrates this and the industry reports there is 2.5x more financial non-malware circulating, which is even more insidious because it’s undetectable. Conducting transactions online therefore does expose login credentials to banking, financial and other online services.
Browser isolation or Internet isolation is a new technique that physically insulates the user’s online activity from their device and network. BankVault isolates and extends this by also separating keyboard input to ensure Passwords, PINs, CVV’s, etc., are never intercepted.
It builds pristine-remote virtual machines instantly which display in the user’s browser. The result is a graphical proxy of the web and an illusion of a keyboard on the user’s mobile. Together these technologies sidestep all potential endpoint malware on the local network and device itself.
BankVault allows users to even work from a compromised device, without exposing input of login credentials.
Key Features
- Absolute Ingonito
- Keyloggers
- Man-in-the-Browser
- Ransomware/viruses
- Workstations
- Clientless – no software or plugins
- Screen scraping
- Man-in-the-Middle
- Invisible to Hackers
- Mobiles
Secure, anonymous and untraceable from the hackers on the network.
Graeme Speak
CEO/Founder BankVault.com
BankVault.com
BankVault is a cybersecurity innovator releasing technologies to secure users from any hacker malware on the users devices or network. The products are browser based web services which completely sidestep user devices and any potential malware that may exist on them. BankVault is used by institutions to secure external customers, and by individuals to take control of their own security.